The Ultimate Guide To Updating Java Certificates Keystore
Wondering how to better manage and protect your digital certificates and keys?
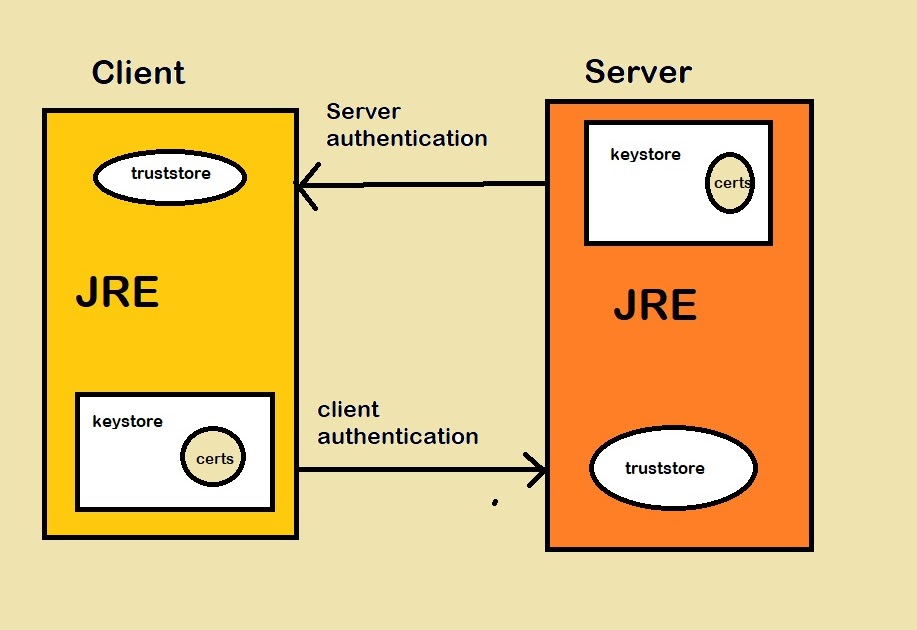
Updating your Java certificates keystore is a crucial step towards enhancing the security of your applications and online transactions. A keystore, in simple terms, is a secure repository for storing digital certificates and their associated private keys. These certificates are essential for establishing secure connections, verifying the authenticity of parties involved in online interactions, and encrypting sensitive data.
Updating your Java certificates keystore offers several benefits. Firstly, it helps mitigate security vulnerabilities by ensuring that your certificates are up-to-date and compliant with the latest security standards. Secondly, it allows you to seamlessly manage multiple certificates and keys, simplifying their deployment and renewal processes. Additionally, it enhances the overall reliability and efficiency of your Java applications, contributing to a smoother user experience.
To delve deeper into the practical aspects of updating your Java certificates keystore, we will explore best practices for keystore management, common challenges encountered during the update process, and effective strategies for maintaining a robust and secure keystore.
Update Java Certificates Keystore
Updating your Java certificates keystore is a critical aspect of maintaining a secure and reliable digital infrastructure. It involves managing, protecting, and updating the digital certificates and keys stored in a keystore, which is a secure repository for these credentials.
- Key Management: Managing certificates and keys, including their creation, renewal, and revocation.
- Security Best Practices: Implementing robust security measures to protect the keystore from unauthorized access and cyber threats.
- Compliance: Ensuring compliance with industry regulations and standards related to digital certificates and keystore management.
- Troubleshooting: Addressing common challenges encountered during keystore updates, such as certificate errors and keystore corruption.
- Automation: Automating keystore update processes to enhance efficiency and reduce manual intervention.
- Integration: Integrating keystore management with other security systems and applications for a comprehensive security posture.
These key aspects are interconnected and essential for maintaining a secure and up-to-date Java certificates keystore. Effective keystore management involves implementing robust security practices, adhering to compliance requirements, promptly addressing any issues that arise, and leveraging automation to streamline the update process. By considering these aspects, organizations can safeguard their digital assets, protect against cyber threats, and ensure the integrity and reliability of their Java applications.
Key Management
Key management is a fundamental component of updating and maintaining a secure Java certificates keystore. It encompasses the creation, renewal, and revocation of digital certificates and keys stored within the keystore. Each of these actions plays a vital role in ensuring the integrity and security of the keystore.
Creating certificates and keys involves generating unique digital identities for entities such as websites, servers, and individuals. These certificates contain essential information, including the public key, which is used for encrypting data, and the private key, which is used for decrypting data. Managing these certificates and keys effectively requires a systematic approach to ensure their proper generation, distribution, and storage.
Renewal of certificates and keys is crucial to maintain their validity and prevent security vulnerabilities. Certificates have a limited lifespan, typically ranging from a few months to several years. Renewing certificates before their expiration ensures that they remain active and trustworthy. Key renewal, on the other hand, may be necessary if a key is compromised or lost. Proper key management practices include establishing a regular renewal schedule and having robust backup and recovery mechanisms in place.
Revocation of certificates and keys is essential when they are no longer needed or have been compromised. Revoking a certificate or key effectively marks it as invalid, preventing its further use. This action is particularly important in cases of security breaches or when an employee leaves the organization. Prompt revocation helps mitigate potential risks and maintain the overall security of the keystore.
In summary, key management is an indispensable aspect of updating Java certificates keystores. It involves creating, renewing, and revoking certificates and keys to ensure their validity, security, and reliability. Organizations must implement robust key management practices to safeguard their digital assets and maintain a secure IT infrastructure.
Security Best Practices
Implementing robust security measures is paramount to the task of updating and maintaining a secure Java certificates keystore. These measures serve as a defense mechanism, safeguarding the keystore from unauthorized access and a range of cyber threats that could jeopardize its integrity and the security of the applications that rely on it.
- Encryption:
Encryption plays a critical role in protecting the confidentiality and integrity of data stored within the keystore. By encrypting sensitive information, such as private keys and certificates, organizations can minimize the risk of unauthorized access and data breaches. - Access Control:
Access control mechanisms, such as role-based access control (RBAC) and attribute-based access control (ABAC), are essential for regulating who can access and manage the keystore. By implementing granular access controls, organizations can limit exposure to sensitive data and reduce the risk of internal security breaches. - Logging and Monitoring:
Logging and monitoring systems provide visibility into keystore activities, allowing organizations to detect and respond to suspicious behavior. By monitoring keystore access logs and system events, organizations can identify potential security threats and take prompt action to mitigate risks. - Regular Security Audits:
Regular security audits are crucial for assessing the effectiveness of security measures and identifying areas for improvement. By conducting thorough security audits, organizations can proactively identify vulnerabilities and implement necessary countermeasures to strengthen the security posture of their keystore.
In summary, implementing robust security best practices is an integral part of updating Java certificates keystores. By adopting these measures, organizations can significantly enhance the security of their keystores, protect against cyber threats, and maintain the confidentiality and integrity of sensitive data.
Compliance
Compliance with industry regulations and standards is a crucial aspect of updating and maintaining Java certificates keystores. Adhering to these requirements ensures that keystores are managed and protected in a manner that aligns with best practices and legal obligations.
- Regulatory Compliance:
Organizations must comply with industry regulations and standards related to digital certificates and keystore management. These regulations may vary depending on the industry and jurisdiction, but they typically include requirements for data protection, encryption, and access control. - Security Standards:
Keystores should be managed in accordance with recognized security standards, such as ISO 27001 and NIST SP 800-53. These standards provide a framework for implementing robust security measures to protect keystores from unauthorized access and cyber threats. - Industry Best Practices:
Organizations should follow industry best practices for keystore management, such as those recommended by the Certificate Authority/Browser (CA/B) Forum and the National Institute of Standards and Technology (NIST). These best practices provide guidance on key generation, storage, and usage to ensure the integrity and security of keystores. - Internal Policies and Procedures:
Organizations should establish internal policies and procedures for keystore management that are aligned with industry regulations and standards. These policies should define roles and responsibilities, key management processes, and incident response procedures.
Compliance with industry regulations and standards is essential for maintaining the security and integrity of Java certificates keystores. By adhering to these requirements, organizations can mitigate risks, protect sensitive data, and maintain the trust of their customers and stakeholders.
Troubleshooting
Troubleshooting is a critical component of updating Java certificates keystores. It involves identifying and resolving common challenges that may arise during the update process, such as certificate errors and keystore corruption. These challenges can be caused by various factors, including incompatible software versions, incorrect configurations, or system errors.
Certificate errors can occur when the keystore contains invalid or expired certificates. These errors can prevent applications from establishing secure connections or accessing sensitive data. Keystore corruption, on the other hand, can occur due to hardware failures, software bugs, or malicious attacks. A corrupted keystore can render certificates and keys inaccessible, compromising the security of the system.
Effective troubleshooting requires a systematic approach. It involves analyzing error messages, examining keystore configurations, and utilizing diagnostic tools. Resolving certificate errors may involve renewing or replacing expired certificates, while keystore corruption may require restoring the keystore from a backup or rebuilding it entirely.
By promptly addressing troubleshooting challenges during keystore updates, organizations can maintain the integrity and security of their keystores. This helps prevent disruptions to critical applications, protects sensitive data, and ensures compliance with industry regulations.
Automation
In the context of "update java certificates keystore," automation plays a pivotal role in streamlining keystore management and reducing the burden of manual intervention. Automating keystore update processes offers several key benefits:
- Reduced Operational Costs: By automating keystore updates, organizations can significantly reduce the time and resources required for manual updates. This can lead to cost savings and increased operational efficiency.
- Improved Security: Automated updates can help ensure that keystores are always up-to-date with the latest security patches and configurations. This reduces the risk of vulnerabilities and enhances the overall security posture of the organization.
- Increased Efficiency: Automation eliminates the need for manual intervention, freeing up IT staff to focus on more strategic tasks. This can improve overall productivity and efficiency.
- Reduced Human Error: Manual updates are prone to human error, which can lead to mistakes and security breaches. Automation eliminates this risk, ensuring that keystore updates are performed accurately and consistently.
Organizations can implement automation in various ways. One common approach is to use scripts or software tools to automate the process of generating, renewing, and installing certificates and updating keystore configurations. By leveraging automation, organizations can streamline keystore management, improve security, and enhance the overall efficiency of their IT operations.
Integration
Integrating keystore management with other security systems and applications plays a crucial role in updating and maintaining Java certificates keystores. By connecting the keystore to a broader security ecosystem, organizations can enhance their overall security posture and gain valuable benefits:
- Centralized Security Management: Integrating keystore management with a centralized security platform allows for the management of all security systems and applications from a single console. This simplifies security operations, improves visibility, and enhances overall control.
- Automated Security Response: Integration enables automated security responses to keystore events. For example, if a certificate is revoked or compromised, the system can automatically trigger actions such as certificate renewal or key rotation.
- Enhanced Threat Detection and Prevention: By integrating keystore management with security analytics tools, organizations can gain insights into keystore activity and identify potential threats. This enables proactive measures to prevent security breaches.
- Improved Compliance Reporting: Integration facilitates the generation of compliance reports by collecting data from multiple security systems and applications. This simplifies the process of demonstrating compliance with industry regulations and standards.
Integrating keystore management with other security systems and applications is essential for maintaining a comprehensive security posture. By leveraging these integrations, organizations can streamline security operations, enhance threat detection and prevention, and simplify compliance reporting, contributing to the overall security and resilience of their IT infrastructure.
Frequently Asked Questions
This section addresses frequently asked questions (FAQs) related to "update java certificates keystore" to clarify common concerns or misconceptions.
Question 1: What is the purpose of updating a Java certificates keystore?
Updating a Java certificates keystore is crucial for maintaining the security and integrity of digital certificates and keys used for authentication and encryption in Java applications. It ensures that the keystore contains the latest and valid certificates, reducing the risk of security vulnerabilities and ensuring compliance with industry regulations.
Question 2: How often should I update my Java certificates keystore?
The frequency of keystore updates depends on several factors, including the expiration dates of certificates, changes in security requirements, and industry best practices. It is generally recommended to update the keystore regularly, such as every six months or annually, to ensure that it remains secure and up-to-date.
Question 3: What are the benefits of automating keystore updates?
Automating keystore updates offers several benefits, such as reduced operational costs, improved security, increased efficiency, and reduced human error. Automation eliminates the need for manual intervention, ensuring that updates are performed consistently and accurately, reducing the risk of errors and enhancing the overall security posture.
Question 4: How can I integrate keystore management with other security systems?
Integrating keystore management with other security systems, such as centralized security platforms and security analytics tools, enhances the overall security posture. This integration enables automated security responses, threat detection and prevention, centralized security management, and simplified compliance reporting.
Question 5: What are the best practices for keystore management?
Best practices for keystore management include implementing robust security measures, adhering to industry regulations and standards, managing keys effectively, and regularly conducting security audits. These practices help ensure the confidentiality, integrity, and availability of certificates and keys stored in the keystore.
Question 6: What are the common challenges encountered during keystore updates?
Common challenges during keystore updates include certificate errors, such as expired or invalid certificates, and keystore corruption. These challenges can be addressed through proper troubleshooting methodologies, such as analyzing error messages and utilizing diagnostic tools.
By understanding these FAQs, you can gain a comprehensive understanding of the importance of updating Java certificates keystores and the best practices involved.
For further information and guidance, refer to the following resources:
Conclusion
Updating Java certificates keystores is a critical aspect of maintaining a secure and reliable IT infrastructure. By implementing robust security measures, adhering to industry regulations, and adopting best practices, organizations can safeguard their digital assets and protect against cyber threats. Automation and integration with other security systems further enhance the efficiency and effectiveness of keystore management.
Organizations must prioritize the regular updating of their Java certificates keystores to ensure the validity and security of their digital certificates and keys. This proactive approach contributes to a strong security posture, protecting sensitive data, maintaining compliance, and fostering trust among customers and stakeholders.
How To Effortlessly Open Any File On Your IPhone: A Step-by-Step Guide
Expert Queencreek Energy Server Services For Seamless Operations
The Ultimate Guide To NGFT Trading: Understanding The Basics